Public records are just that – they’re records which belong to the public interest. Court and incarceration records are no exception to that. It’s in the interest of the people to know who has been arrested, when, where, and why. Not just to keep the people safe from crime, but to keep the people informed of the government’s doing.
What is a National Criminal Database?
In our last article, “What is an SSN Trace”, we talked about the importance of a SSN Trace for the background checking process. It helps identify aliases and addresses that the applicant may have used but did not report on their application. This time, we’ll talk about the next step in the background checking process: National Criminal Database Search.
What is an SSN Trace?
When an employer conducts a background check on an applicant, there are a handful of steps that must be followed to ensure accuracy. Part of that process is what’s called an SSN Trace.
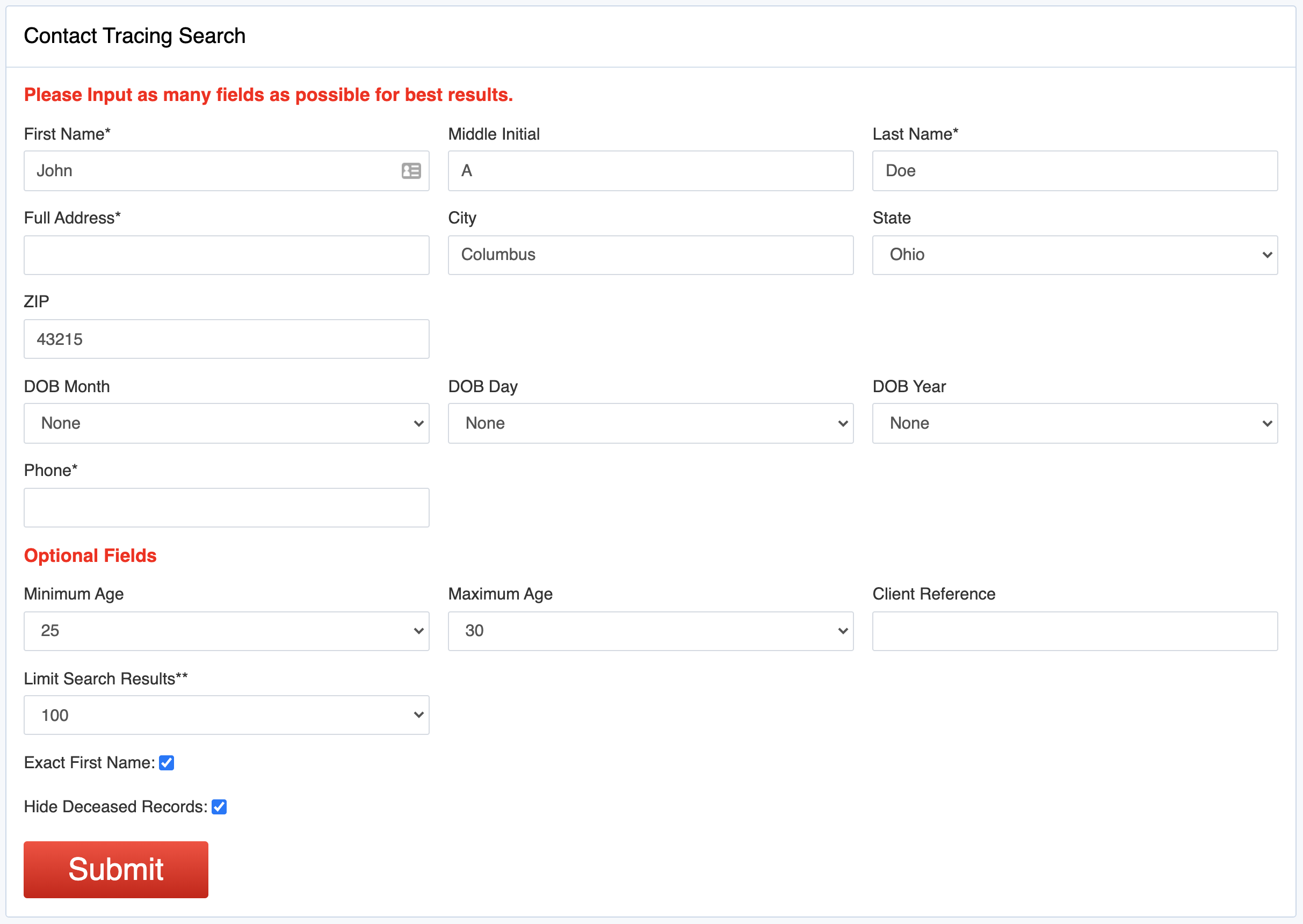
Contact Tracing – What Martin Data is Doing to Help
In our previous articles, we spoke to a lead contact tracer named Steven who worked for the health department of a major Midwest city. Our questions mostly concerned what his job looks like on a day-to-day and what kinds of tools he uses to do his work. To continue our Contact Tracing series of articles, we’d like to explore some of the things Martin Data is doing to help the industry.
When in early March, when it became obvious that COVID-19 was going to be a world-changing crisis, the Martin Data team got together and brainstormed about how we could help.
What is Contact Tracing? And How is it done?
Last time we talked about what contact tracing is and why it’s so important. We interviewed Steven, a lead contact tracer for a large mid-west city’s health department, and he walked us through what his day typically looks like. This time we’ll continue our interview with Steven and explore some of the tools and methods that these contact tracers use to find individuals who may have been exposed.
We continue our interview below, asking Steven what sort of information is most useful in his course of work
What is Contact Tracing? And why is it so important?
An interview with a COVID-19 contact tracer
Contact Tracing is the process of finding and contacting individuals who may have been exposed to an infectious disease. Sometimes it’s a result of them having been at a location or event that had infected people and sometimes it’s a result of them having come in direct contact with an infected individual. It’s a technique that dates back centuries.
One of the most famous uses of this technique was to identify Mary Mallon (1969-1936), aka: the infamous “Typhoid Mary” who infected upwards of 50 people and ultimately caused the death of at least 3. I highly suggest reading her fascinating history on both the NIH website and Wikipedia
GDPR: A Year In Review: Part 2
In our previous article, we spoke about some of the copy-cat laws that have popped up within the United States in response to the GDPR – things like California’s CCPA and New York’s SHIELD law. In this article, we wanted to focus on the ever changing landscape of regulations within the US.
Pitfalls of individual state (and local) regulations are not new to businesses nor the consumer. I’m sure a good portion of our readers know what it’s like trying to find alcohol in a dry county – or perhaps you’ve noticed the incredible differences in gun laws in one state to the next.
GDPR: A Year in Review: Part 1
It’s been one year since the GDPR (General Data Protection Regulation) was implemented. We wanted to see what other regulations have passed since then as a result. What seedlings have sprouted?
The importance of credentialing: A case study
Part of our credentialing process is to make sure that there is one “responsible party” on file. This is the person who signs on the dotted line saying that they will not abuse the service, that they’ll pay the bill, and all that fun stuff. Read More
How long does it take for a new address to appear in our data?
Believe it or not, this is a question we don’t get asked very much – and you’d think we would! It’s a very important measure of data quality. If I move to a new house today, how long will it take for that new address to appear on USInfoSearch? What sorts of changes might cause that new address to appear on USInfoSearch?
The short answer? Around 2 weeks. The long answer? That all depends…
How do we protect our data?
Data security is a big concern in today’s world. So how does USInfoSearch secure its data from unauthorized access?
2-Factor Authentication – All accounts on USInfoSearch are protected using 2-factor authentication. When you enter your username and password, we’ll send you a text message with a validation code. You’ll have just a few minutes to enter that code in order to complete the login process. This ensures that only the account holder can gain access to our data and your account.